High technological advancement is undoubtedly a boon. It has made almost all tasks much easier, thus saving lots of manpower and time. However, high technology has simultaneously resulted in many remarkable security threats.
The moment you start reading the e-newsletter, there will be at least one case related to cyber threat or fraud. Isn’t it? Now, if you are running an organization and getting nightmares about the mushrooming rate of cybercrimes, then why not look into cybersecurity risk management?
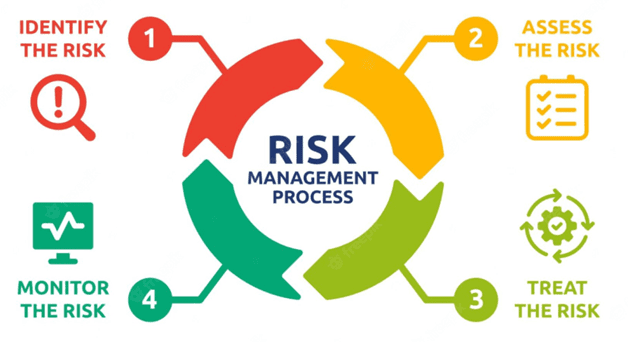
Are Cyberattacks Random?
No, cyberattacks are pre-planned against an organization. Markers of imminent attack mention the areas of businesses to attack on the dark web. In this case, the registration takes place in the form of similar domain names that can be utilized for phishing attacks.
Even confidential information, including user account credentials, is illegally sold. Regularly maintaining a vulnerability management program can reduce the risks associated with cybersecurity. A cyber-attack maturity assessment can help bolster security activities.
What are the Different Types of Risks in Cybersecurity?
As a business owner, it is better to start with some vital steps that will protect your organization from harmful effects of cyber threats. If it is a top priority, then it may seem easier to prevent unwanted losses.
Having a proper understanding and preparation for malware, DDoS and ransomware attacks will be a good idea. The malicious incidents that lead to high losses to businesses include third-party risks, phishing attacks, and infiltration by malware.
What is Cybersecurity Risk Management all about?
Cybersecurity risk management is becoming a vital part of almost every organization. It is a strategy related to implementing processes that help in identifying, addressing, and repairing cyber threats.
The process is ongoing. High emphasis is placed on technologies, procedures, training programs, administrative practices, and physical controls for protecting digital assets.
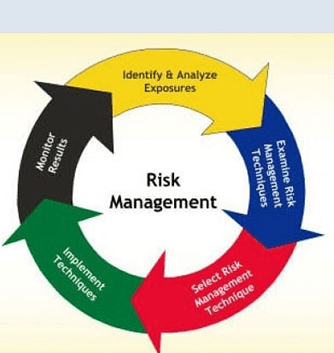
The assets also include applications and data. Cybersecurity is a technical discipline that involves implementing activities ranging from anti-malware to firewall implementation. It also includes encryption and cryptography for protecting system information.
Is it possible to assess an organization’s risk rate?
In the context of cybersecurity, risk assessment followed by management refers to practices to identify, control, mitigate, and balance threats. Assessing the amount of risk an organization takes when carrying out operations becomes easy.
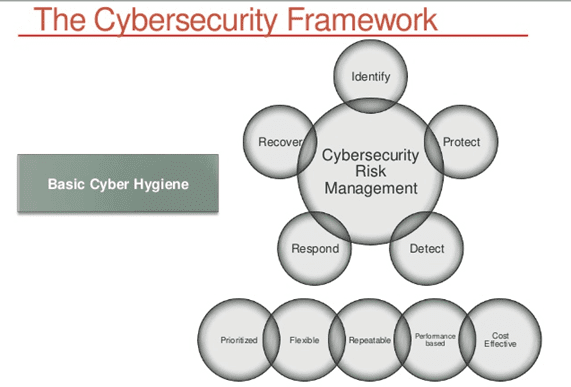
When conceptualizing variable disciplines, risk is a highly concrete factor. Real metrics for measurement and decision-making at the right time may help protect theprotect the company’s revenue.
What Are Some Remarkable Benefits of Cybersecurity Risk Management?
Today, cybersecurity risk management is a highly important practice that helps organizations stay safe. It prevents the harm caused by data breaches, cyberattacks, and additional cybercrimes.
Are you aware of some of the remarkable benefits of cybersecurity risk management practices? If not, then below are some of the highly vital ones:
- Improvement in visibility—Implementing proper risk management strategies may help organizations reap the benefits of improved visibility in cybersecurity posture. Experts involved may easily identify areas that demand additional security controls, thus responding to threats properly.
- Enhanced security rate – As the rate of cyber-attacks becomes lower, businesses can mitigate the overall impact in case of a breach. With proper understanding and response to potential threats, proper action can be taken to protect the system and data.
- Improvement in decision-making power—With proper understanding of the level of potential risks and consequences, business owners can make the best decisions to control threat attacks. This may open the door to highly effective resource allocation and system design decisions.
- Highly efficient security strategy—Advanced risk management procedures can help organizations develop a highly efficient security strategy by simply focusing on threats that pose high risk. This will allow professionals to prioritize efforts related to security risk management and allocate resources.
- Compliant with regulations—Many organizations need to maintain specific levels of standards related to cybersecurity. They also need to comply with certain regulations, such as GDPR, PCI DSS, and many more. A robust risk management strategy will help organizations meet and maintain regulatory compliance requirements.
The right programs related to cybersecurity risk management allow businesses to prioritize risk levels. They also allow businesses to apply the right security controls to minimize the impact of threats actively.
What are Some of the Best Practices Related to Cyber Risk Management?
By carrying out some of the best practices related to cyber risk management may become easy to prevent your business from unwanted threats. Before it becomes too late, below are some points to consider for preventing huge losses:
- Having an idea about the IT environment and assets—The first step is to Have an in-depth knowledge of the organization’s IT assets and environments. Continuous monitoring of these may help prevent unwanted cyber-attacks.
Also, more resources followed by closely guarding your business assets may be a safe measure.
- Development of robust risk management strategy—Engaging in risk management without an in-depth thought management plan may prove detrimental. That is why companies must develop some of the best strategies and continue updating them.
First, it’s better to identify risk tolerance and develop a risk profile before strategizing. The risk management should include decent escalation plans, employee roles, and key stakeholders.
Coming up with some of the best practices for employees and integrating some training may also be beneficial.
- Embedding cybersecurity risk management in culture and values—Developing cybersecurity risk management programs and processes and implementing them across the business is one more best practice. It is also better to document almost all the strategies, plans, and procedures and communicate them to stakeholders.
Also, embedding cybersecurity risk management in an organization’s culture and values may prevent unwanted threats.
- Carrying out adaptive and actionable risk management steps—Without proper risk identification, risk management plans may seem worthless. As the level of online fraud is continuously evolving, it is good to stay updated with some decent technical practices.
As the company’s risk frame may change, gaps and updates should be reviewed regularly for highly effective security measures. With the right type of cybersecurity risk mitigation and actionable techniques, companies can secure their IT environment and highly valuable digital assets.
- Enforcing strict security protocols—One vital practice is implementing comprehensive and highly intuitive security measures. Employing automated patching practices and a managed web application firewall may allow for effective risk mitigation.
At the same time, you may enforce strict authentication policies and extend security steps to almost all devices. Enforcing highly strict security protocols may prove effective for both remote and on-site workers.
- Ensuring real-time and reliable visibility—Intruders can easily reach anywhere without causing much hassle. That is why cybersecurity risks are evolving exclusively almost everywhere within the organization.
Implementing real-time and reliable visibility in the dynamic risk profile may benefit an organization. If the risk mitigation steps are based totally on real-time insights, they may prove to be more effective.
Taking some preventative measures beforehand may help in preventing unwanted cyberattacks.
As a Final Word!
From the above, it is clear that business processes also change as vulnerabilities multiply with time. This is giving rise to high-level risks for organizations, too.
Considering budget and time, providing total protection from almost all types of risks is unattainable. Hence, with an ongoing cybersecurity risk management program, businesses may experience exclusive benefits in terms of safety from threats.
Reference URLs:
https://www.indusface.com/blog/6-best-practices-in-cyber-security-risk-management
https://www.rapid7.com/fundamentals/what-is-cybersecurity-risk-management
https://www.kiteworks.com/risk-compliance-glossary/cybersecurity-risk-management








