As an IT professional, are you aware that several software packages are introduced into the market at an interval of almost a minute? They have undoubtedly resulted in lots of convenience for both users and service providers.
However, it has also resulted in an increase in the level of vulnerability. An increase in the number of threats accelerates complexity. If proper precautions are not taken at the right time, then it may lead to great havoc.
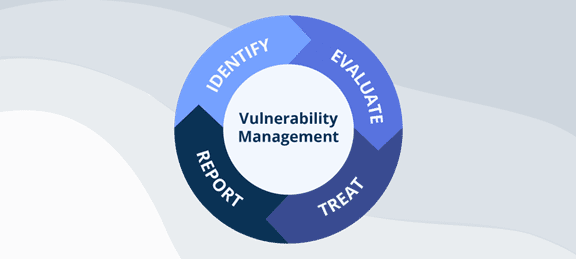
The role of vulnerability management shines a bright light on how every organization is prepared to face cyber-attacks.
What is the Strategy of Vulnerability Management all about?
Over the years, vulnerability management has undergone a highly sophisticated procedure through manual processing. Technically, it refers to a multi-stage process for handling almost every type of cyber risk for an organization.
It is inclusive of the process to identify weaknesses in security in the following sectors:
- Infrastructure
- Cloud-based system
- Application
With time, the process is becoming highly essential as the rate of cyber risks is mounting for almost every type of organization. Vulnerability management requires highly specialized tools for identifying and prioritizing risk factors.
Based on the inferences, designing and implementing proper strategies will become easy. Those strategies may help prevent any type of breach in the IT system security. A procedural system is carried out to identify the following:
- Framework for prioritizing and treating threats
- Laying the foundation for long-term operation and needs of any business
Overall, vulnerability management is the strategy of evaluating, treating, and reporting vulnerabilities to prevent cyber-related threats. Remediating security-related weaknesses and flaws in IT system software will seem easier.
In Which System Does Vulnerability Management Work?
From above, it is clear that vulnerability management is a proactive and automated process that keeps computer systems, applications, and networks in safe hands. Proper identification, assessment, and addressing of potential security-related weaknesses can minimize damage.
This specific strategy aims to reduce an organization’s chances of risk exposure by mitigating vulnerabilities to the maximum. Vulnerability management must be a continued procedure to keep up with new and emerging threats and changes.
Now, threat and vulnerability management uses a wide range of tools for preventing cyber threats. This specific program uses many components.
Some of the essential ones are as follows:
- Vulnerability scanners—Usually, vulnerability scanners perform a series of tests against all systems and networks to identify common flaws.
They include attempts to exploit vulnerabilities, guessing default passwords and accounts, plus gaining access to restricted areas.
- Asset discovery and inventory—The IT industry is all about tracking and maintaining records of almost all types of devices. Accessing the company’s digital environment may seem highly complex.
This is why highly experienced professionals turn to asset inventory management systems. These systems may provide visibility to the assets of companies, along with their location and resource usage.
- Patch management—The patch management tool helps companies keep their computer systems ready with the latest security patches. Solutions associated with it check for updates and prompt users regarding their availability.
Some exclusive patch management systems open the gateway for deploying patches across multiple computers. This not only reduces the hassles for professionals but also makes it easier to ensure security for large fleets of machines.
- Penetration testing—The penetration testing software is designed exclusively for IT experts to discover and exploit vulnerabilities in computer systems. Typically, this exclusive package provides a graphical user interface, making it easier to launch attacks.
Some products offer automation features to speed up the entire process. Stimulation of attacks will let testers identify vulnerable spots in systems.
- Threat intelligence is specific process that allows organizations to track, monitor, analyze, and prioritize threats to ensure higher protection. The data is collected from various sources, such as databases and advisories.
Such exclusive solutions help companies identify ongoing trends and patterns. They may also help indicate a security breach or attack in the future.
- Security configuration management—This process ensures that the devices in use are configured securely. Any change made to the device security settings can be easily tracked and approved to prevent malicious attacks.
The attached tools are compliant with security policies and help in easy scanning of devices and networks for vulnerabilities. Also, tracking remediation actions and generating reports will no longer be a hassle.
- Remediation vulnerabilities—Remediation involves identifying vulnerabilities, taking appropriate steps, and generating remediation tickets. This will help IT professionals continue with security measures smoothly.
Also, the remediation tracking tool is highly vital to ensure that the misconfiguration and vulnerability are addressed properly.
- Security incident and event management—The security incident and event management software package consolidates an organization’s security information and considers real-time events.
The solutions are designed to give organizations visibility to all activities taking place around the IT infrastructure. This includes monitoring network traffic, identifying devices that connect internal systems, and keeping track of user activities.
Those days have become pages of history when manual system scanning and isolated networks helped to create vulnerability. With the advancement of technology today, a high level of protection is required against the constant onslaught caused by cyber-attacks.

Advanced technology is required with high-paced automated scanning of the environment and cloud connection. Constant live updates in terms of vulnerability management may help prevent further destruction.
The time has come to demystify the risk management lifecycle of cyber risk.
How are Vulnerabilities Categorized for Actions to Build Around?
Do you know that vulnerabilities are categorized for actions to build around accordingly? At the evaluation stage, the risks are organized into a specific plan for actions to be built around.
Some vital factors that you need to take into consideration at the time of ranking vulnerabilities include the following:
- Various types of exploits
- Level of damage
- Probability of any going-to-be attack
- Cost associated
- Time consumed for securing a threat
Now, the vulnerability rates of severity of risks associated are:
- Low (ranging between 0-to-4)
- Medium (ranging between 4-to-7)
- High (ranging between 7-to-10)
The scores may serve as a starting point to identify vulnerabilities. The team of professionals generally considers the risks posed by every type of vulnerability about organizations.
What are the Various Types of Vulnerabilities?
With advancements in technology, the rate of cyber-attacks has also increased. The vulnerabilities have been classified into various categories include:
- Cloud vulnerability—This is a special type of vulnerability that brings up challenges. At times, users are also in a fix regarding their responsibilities in terms of protection.
- Application vulnerability refers to software errors that can be easily exploited to breach the security level of a network.
- Configuration errors—If the network systems are not configured properly, configuration errors may result. They are one of the most basic errors.
Even after updating and patching software packages, some potential vulnerabilities may exist. These may include a lack of encryption for stored data. Some companies take security seriously but fail to recognize the upcoming threats.
The Final Goal of Vulnerability Management!
Organizations are striving hard to lower the risks associated with cyber-attacks. They prioritize and remediate vulnerabilities that may pose higher risks. Highly effective and efficient vulnerability management planning may make it easy for the IT team to save time and money.
It also helps in lowering the risk level to the maximum.
Reference URLs:
https://vulcan.io/basics/the-ultimate-guide-to-vulnerability-management/#0
https://purplesec.us/learn/vulnerability-management-lifecycle








