Introduction
Microsoft’s Power Platform has rapidly evolved into one of the most impactful low-code platforms, enabling business users and professional developers alike to build apps, automate workflows, and deliver analytics. But with this democratization comes responsibility. Governance, security, and compliance are no longer optional; they are essential. This article introduces the concepts, outlines risks, and frames the governance journey.
Topics covered:
– Why governance is critical for enterprises adopting Power Platform.
– The risks of shadow IT, unmanaged connectors, and orphaned apps.
– The balance between empowering citizen developers and maintaining IT oversight.
– Microsoft’s tools for governance: Admin Center, PowerShell, DLP, and the CoE Starter Kit.
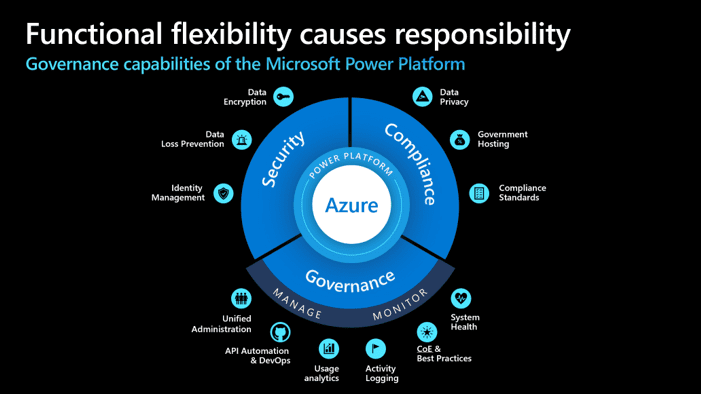
Governance Fundamentals
Governance spans multiple dimensions: environments, security, data, and compliance. In this section I break these down and provide practical guidance on how to implement guardrails.
Steps to establish governance fundamentals:
1. Define roles: IT admins, citizen developers, fusion teams.
2. Establish policies: what can be built, where it can be deployed.
3. Implement DLP policies immediately to prevent risky data flows.
4. Use the Admin Center to monitor capacity and usage.
Example risk:
Without DLP, a flow might copy customer data from Dataverse to Dropbox; creating compliance risks.
With governance, this risk is blocked.
Environment Strategy
A well-defined environment strategy is the backbone of governance.
Recommended structure:
– Default Environment → restricted for enterprise apps.
– Sandbox → experimentation and prototyping.
– Dev → controlled environment tied to source control.
– Test/UAT → validation and approvals.
– Prod → strictly governed for mission-critical apps.
– CoE Environment → dedicated to Center of Excellence toolkit.
Provisioning with PowerShell:
Install-Module -Name Microsoft.PowerApps.Administration.PowerShell
Add-PowerAppsAccount
New-AdminPowerAppEnvironment -DisplayName “Sandbox” -Location “Europe” -EnvironmentSku “Sandbox”
Real-world example:
A global bank provisions environments per region (US, EU, APAC) with local admins, while enforcing tenant-level DLP policies.
Data Loss Prevention (DLP) and Connector Management
DLP policies prevent data exfiltration and ensure compliance.
Connector groups:
– Business group: Dataverse, Office 365, SQL.
– Non-business group: Twitter, Dropbox, Gmail.
– Blocked: explicitly prohibited.
PowerShell example:
New-AdminDlpPolicy -PolicyName “CorporatePolicy”
Set-AdminDlpPolicy -PolicyName “CorporatePolicy” `
-BusinessConnectorGroups @(“shared_office365”, “shared_sql”) `
-NonBusinessConnectorGroups @(“shared_twitter”, “shared_gmail”)
Industry example:
In healthcare, DLP prevents PHI (Protected Health Information) from leaving Dataverse into non-compliant connectors like Gmail.
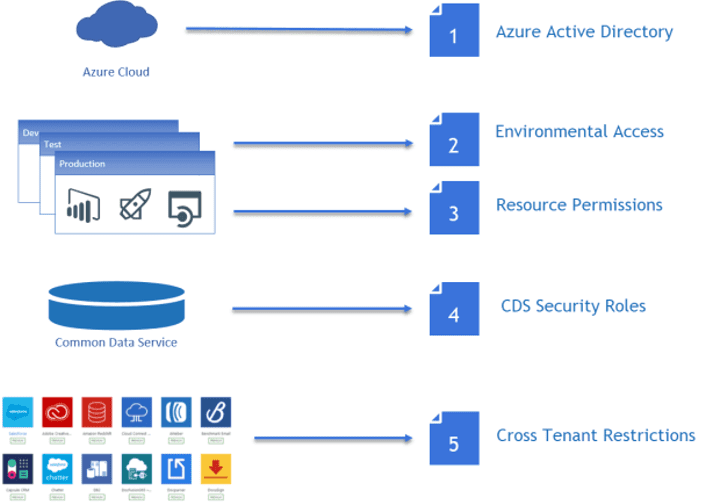
Identity and Access Management
Identity is enforced via Azure AD.
This enables Conditional Access, MFA, and Privileged Identity Management for admins.
Dataverse adds fine-grained RBAC:
– Role-based access for apps and data.
– Row-level security for table data.
– Field-level security for sensitive columns.
Example:
A hospital app uses Dataverse row-level security to ensure doctors only see their own patients, not others.
Monitoring and Telemetry
Visibility is crucial to governance.
Admin Center features:
– Capacity usage monitoring.
– App usage and flow run analytics.
– Environment-level DLP reporting.
Export logs with PowerShell:
Export-AdminPowerAppEnvironmentLog -EnvironmentName “Prod” -Output “C:\logs\env.json”
Advanced monitoring:
– Integrate with Azure Monitor.
– Send logs to Log Analytics Workspace.
– Feed into SIEM (Azure Sentinel, Splunk).
Scenario:
Suspicious connector use (e.g., SharePoint + Twitter) can trigger Sentinel alerts and automated response actions.
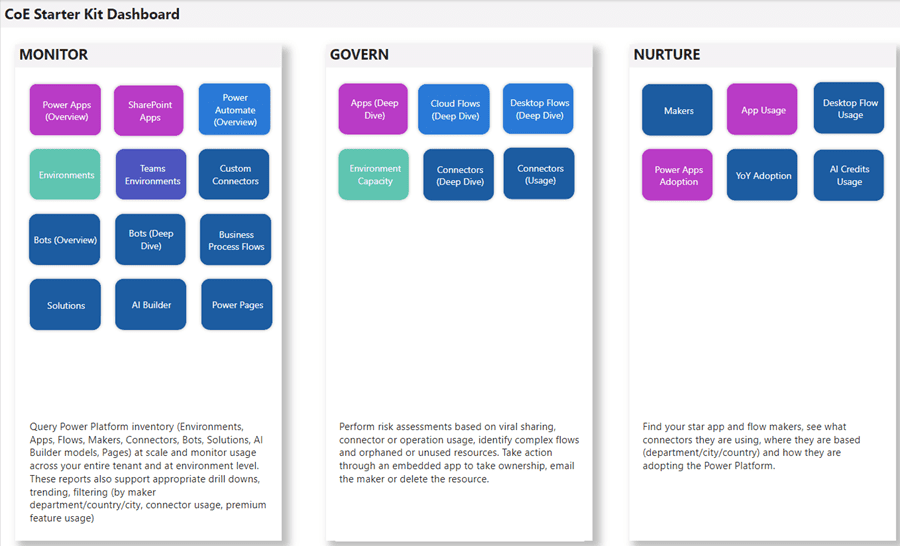
The Center of Excellence (CoE) Starter Kit
The CoE Starter Kit provides governance-in-a-box.
Components:
– Power Automate flows → inventory and alerts.
– Power Apps → admin apps for reviewing apps/flows.
– Power BI dashboards → adoption, risk, usage.
– Dataverse → central repository.
Deployment steps:
1. Provision dedicated CoE environment.
2. Import solutions from GitHub.
3. Configure admin connectors.
4. Enable scheduled inventory flows.
5. Review Power BI dashboards.
Example Dashboard metrics:
– Active makers: 150
– Total apps: 520
– Orphaned apps: 33
– High-risk flows: 12
– DLP violations: 8
Advanced Governance Scenarios
Governance evolves with advanced scenarios.
Examples:
– Automating orphaned app cleanup → Power Automate flow detects inactive owners, reassigns or archives.
– Fusion team enablement → citizen dev builds UI, pro dev extends with Azure Functions.
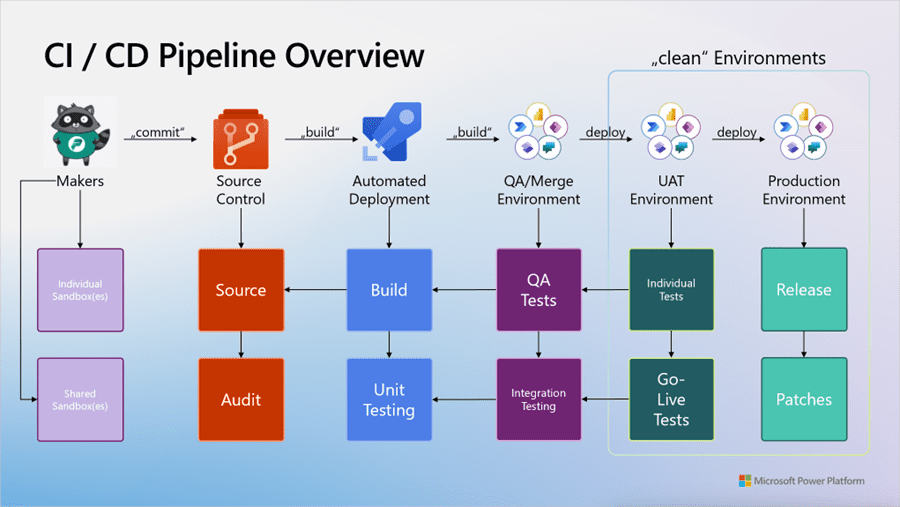
– CI/CD pipelines → Power Platform CLI + Azure DevOps to promote solutions from Dev → Test → Prod.
– Regulated industries → HIPAA, SOX, GDPR compliance mapping.
Best Practices & Enterprise Playbook
Best practices learned across enterprises:
– Adopt environment strategy early to prevent sprawl.
– Apply tenant-level DLP policies before adoption scales.
– Automate governance with PowerShell and CLI.
– Deploy CoE toolkit for visibility.
– Integrate with SIEM for continuous monitoring.
– Foster a governance culture: empower but monitor.
Playbook example:
Step 1 → Provision environments.
Step 2 → Apply DLP policies.
Step 3 → Install CoE toolkit.
Step 4 → Automate monitoring.
Step 5 → Enable fusion teams.
Future Outlook
Power Platform is evolving rapidly.
Emerging trends (2021 and beyond):
– AI Builder integration → governance of AI models.
– Power Automate Desktop → governance of RPA bots.
– Teams integration → governance within collaboration hubs.
– Adaptive governance → policies that adjust as adoption grows.








