Frequent bank frauds are becoming something common day by day. The moment you browse through the Google page or any social media platform, news about some online threats will surprise you.
Some of the most occurring incidents include hacking, unauthorized disclosure of information, attacks related to denial of service, and many more. Has anyone been successful in addressing them?
There is hardly any solution to date, thus leading to heart-rending losses. With the high advent of internet technology, the introduction of threat modeling proves to be the best solution.
Threat Modeling: An Introduction!
As the name speaks, threat modeling refers to the most aggressive procedure of identifying the going-to-be cyber risks. It also helps in prioritizing the same. Making generous application of this specific model may help the IT team to understand the following:
- Nature of threats
- Impact of threats on the network
Additionally, threat modeling may be utilized to analyze dangers that may pose exclusive hampers to computer applications. Based on the potential vulnerabilities, the level of threats can be categorized.
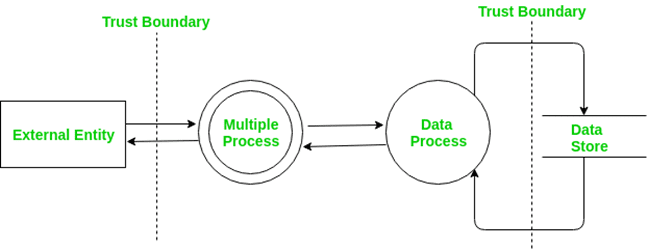
Ref Link https://www.geeksforgeeks.org/threat-modelling/
What Makes Threat Modeling High Demandable?
The mushrooming rate of cybercrime incidents has created a high trauma almost in the minds of everyone. It has even taken a heavy toll on the online community as well. According to recent reports, the exposure to data breaches has reached billions.
Also, the rate of social media-related cybercrime, including robbery, has set a proven track record in annual revenue globally. Almost seventy-five percent of businesses consider insider threats among the most significant concerns of phishing and email scams.
This has even resulted in high investment in cyber security products and services. The overall budget has surpassed trillion dollars. As no fixed time is allotted for cybercrime, safety is the first concern for almost all businesses.
With a whopping in the security breach, smart organizations are on their way to make the application of reliable resources for fighting the epidemic. Though many solutions are available, threat modeling is more sound.
Organizations and individuals planning to go with something extraordinary for security purposes can give a trial to this.
In Which Process Does the Threat Model Work?
The threat model not only assures high protection for network and applications, but it also helps secure business processes and the Internet of Things (IoT). As the model is versatile, a veritable cyber navy may allow the organization to protect itself from many threats. Threat modeling is perfect example of secure-by-design approach, where threats can be identified during the early stages of SDLC (mainly at design phase), in order to shift-left defects.
Overall, the process of threat modeling may vary depending on the type of system that is being examined. It will narrow down the process of coming across threats and benefit the organization manifold.
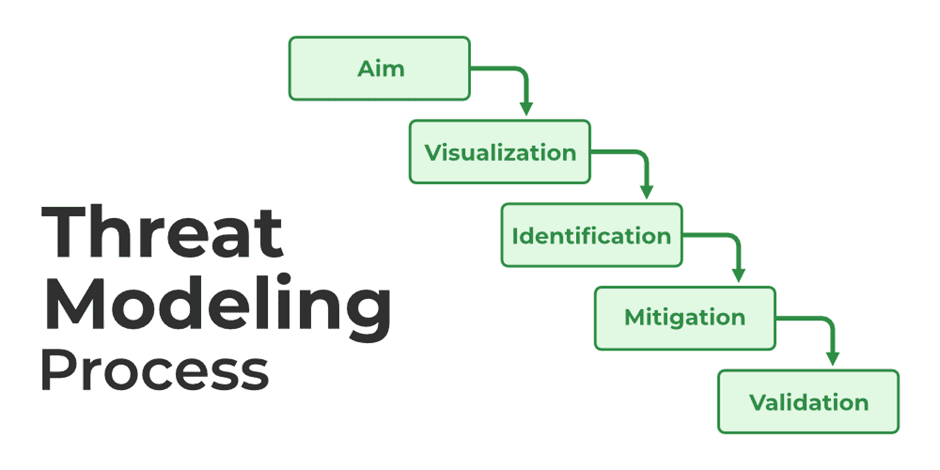
It is possible to identify the type of attacks and defend them. Are you aware that the entire threat modeling process is based on a sequence?
You can perform the steps individually. However, as they are interdependent, all the steps need to be executed together to reach a comprehensive solution. The steps include the following:
- Outlining – Firstly, it is mandatory to understand the concern related to the specific system or application.
- Listing—Next, it is the turn to prepare a list of the assumptions that may cause the threat. This may help in proper identification of changing conditions.
- Identifying – Afterwards, you need to develop a concrete list of almost all types of threats.
- Remedy—Based on the type of threats, the required remedies and elimination steps will be easy to develop.
- Assuring – Finally, one must make sure that the methods for dealing with threats are highly successful and valid.
Now, it is the turn to peep into the four-question framework that helps in organizing the overall concept of threat modeling.
What is the Four Questions Framework?
A list of possible threats may come to the limelight whenever threats occur and have a highly significant impact on the organization. To make the process short and manageable, the four-question framework may lead to easy organization.
The framework includes the following:
- What type of threat is the operation working on?
- What can go wrong during the process?
- What will be the right solution against the threat identified?
- Whether the step taken has been correct or incorrect?
There is no specific way to come up with the right answer to these questions. Properly utilizing structured models can make the process even more efficient. Evaluation of a combination of threats, vulnerability, level of attack, and impact may result in a waste of time.
Instead, refining the search space may help determine the possible threats on which focus can be made.
What are Some Remarkable Benefits of Threat Modeling?
Every process related to cybersecurity needs to be performed correctly to ensure crystal-clear visibility. Similarly, threat modeling may be clear across any IT-based project.
It will also help verify the security efforts. The entire process may help the organization create documents that address dangers related to security, which may help in devising the best ways to fix them.
Ref Link https://www.cymune.com/threat-modelling
A nicely structured threat model will help develop the right process to explain and defend an application’s security posture. Do you want to know the level of effectiveness of threat modeling? Here it is…
- Detecting issues – Detection of problems in the software development life cycle before coding
- Spotting flaws – Spotting the flaws in designing that may get overlooked through traditional testing and code reviewing
- Evaluating attacks – Evaluation of new types of attacks that have not been considered earlier
- Maximizing budget – Maximizing the testing budget may help in efficient testing and reviewing of code.
- Identifying security – Identification of security-related needs remains no more a hassle.
- Remediating threats – Remediating threats prior to the final release of the software may prevent costly debugging and recording
- Assumption of attacks – Assuming attacks that are beyond understanding may prove to be greater and unique security to the application
- Keeping frameworks ahead – Keeping frameworks ahead of attackers will prevent unwanted disruption to the project.
- Deducing components—Highlighting assets along with threat agents may provide control over components that may be attacked by attackers.
- Modeling of the location – Modeling the location of agents related to threats may prevent cracking of the system architecture.
From above, it is clear that threat modeling is popular for providing a clear line of sight across a project for justifying security. The specific model permits rational safety-related decisions.
What are Some Tools Used for Threat Modeling?
The variable threat modeling methodologies that the development team nowadays prefers are STRIDE, DREAD, PASTA, Trike, VAST, CVSS, T-MAP, and Attack Tree. These methodologies may help create a highly effective threat intelligence report, and the team dealing with security and operations can protect IT assets from vulnerabilities.
What are the different types of tools that may prove to be highly effective for threat modeling? The list is endless. Still, some of the most popularly known are:
- Threat modeling tool by Microsoft
- MyAppSecurity
- IriuRisk
- securiCAD
- Tiramisu
- CVSS 3.0
As a final word, threat modeling is not an approach to reviewing code. It is used to complement the entire process of reviewing security code. It will let the reviewers identify the entry points to a specific application and the associated threats at every point.
Reference URLs:
https://owasp.org/www-community/Threat_Modeling_Process
https://www.fortinet.com/resources/cyberglossary/threat-modeling
https://www.synopsys.com/glossary/what-is-threat-modeling.html
https://www.geeksforgeeks.org/threat-modelling








